Sans Help in Software Security
Sans.org has been around for many years helping people secure their internet presents. This is just a sample of the thousands of doc and training they have.
Secure Coding.
Practical steps to defend your web apps
One of the best measures of AppSec maturity is how integrated these processes are with security and IR operations. Despite their concerns about silo mentalities, 67% of respondents have partially integrated AppSec into these operations, and 65% are partially satisfied with this stage of their integration. Another 17% have integrated fully, and 13% are satisfied with this full level of integration. See Figure below
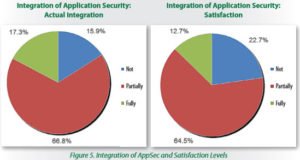
A fully integrated AppSec program can reap benefits in overall security posture and IR capabilities. An AppSec program spans internally developed applications and applications procured from outside vendors. Integrating such a program provides valuable input for the overall enterprise security program, including IR. For example, for a purchased application, a predeployment AppSec review will identify configuration requirements to ensure that the application is used securely. The review will also identify log management/review requirements and establish a baseline for expected application behavior. In case of an incident, this information can be valuable in helping responders identify the incident and analyze a possible compromise of the application.
Link this and much more at Sans.




Leave a Reply