Networking Made Simple
Below is a summary of networking made simple. I hope it helps you to understand networking better. With most operating systems, the lower OSI layers of a physical medium data link with MAC address, network with IP address, and transport with TCP or UDP, and will be understood by both devices. More research is often needed to understand if some of the uppermost layers—such as the session, presentation, and applications layers—are common to both devices.
Some examples of application layer protocols in the industry are Modbus TCP, Ethernet/IP, and Profinet. However, even with compatible layers, both networked devices must support protocol functions.
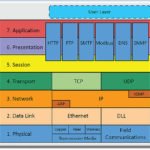
The picture on the left is an old picture from CISCO training courses. This OSI Model has 7 layers and one should understand it before reading more. But then again one only needs to know that if I type a .com or any other dot in a browser I will get there.
Unmanaged versus managed switches
Open Systems-Interconnection OSI
Ethernet network topologies include the bus, ring, and star. Bus and ring are similar to a daisy-chain connection where a single cable hops between each device. Bus topology is a bit obsolete, while the newer ring topology adds fault tolerance. However, most industrial Ethernet installations use a star topology, with some ring connections to reduce cable run distances.
With the star topology, a switch connects devices to a central access point. Ethernet switches come in both unmanaged and managed configurations. There are applications and situations that make sense for unmanaged switches, and there are others where a managed switch is a far better choice.
When connecting a device to a switch, it automatically negotiates to an agreed-upon speed and duplex mode. Auto-negotiation can be tricky and will often fail. It is better to turn off auto-negotiation, using a managed switch, and fix the speed and duplex to a known working setting for both sides. This can be particularly helpful when connecting together devices from different manufacturers.
For a simple network with five or fewer devices in a relatively small area, an unmanaged switch will usually work, and it will always be less expensive than its managed equivalent.
For larger applications with many devices from several manufacturers, consider a managed switch. Often these applications include extensive multicasting, using Ethernet/IP for example, and are spread out over a large area. A managed switch’s configuration and problem-solving features will easily outweigh the cost premium over an unmanaged switch in most complex applications.
IP addresses and MAC addresses are targeted at specific devices. But there are two other types of messages that are targeted at multiple devices: broadcasts and multicasts. It takes a router to stop broadcast messages but managed switches can intelligently route multicast messages to the correct ports by using IGMP snooping. The switch will learn which ports should be receiving multicast messages (by “IGMP Join” messages) and only send messages to those ports, enhancing system performance.
Managed switches can filter out multicast messages used in Ethernet/IP. Managed switches can also prevent the network from shutting down if someone accidentally loops the switches.
If unmanaged switches are mistakenly connected together in a ring, a broadcast storm will occur and shut down the network. Managed switches prevent this by shutting down one path of the ring. If something happens to the working path, the switch changes over to the other path, which also provides a level of redundancy.
Subnetting and networking
The media access control (MAC) address is the “hard” physical address of a device. The address is set during manufacturing and should never change. Although there are exceptions to this, hard coding the MAC address was the original intent of the design. An Ethernet packet cannot enter a device without this address. However, it’s rare that a communication setup or configuration will need this address because another protocol, called address resolution protocol (ARP), usually automatically retrieves it and correlates it to an IP address.
The IP address is the logical address of a device, used to identify an address and network of the specific device. An IP address, such as 192.168.070.001, includes two identifiers: the network address and the host address. The network address helps devices and routers determine where to send messages. The host address identifies the specific device on that network. The subnet mask, such as 255.255.255.000, determines which part of an IP address is the network address and which part is the host address.
The subnet mask determines the portion of the IP address that is network and host. Wherever there are 1s in the mask, the corresponding bit location of the IP address is part of the network address. Wherever there are 0s in the mask, the corresponding bit location of the IP address is part of the host address.
The default gateway address and a router enable connections to other networks. A device can only send and receive Ethernet messages to other devices on its network as determined by the IP address and subnet mask. If a device needs to communicate with a device on another network, a router is required. To get the message to the other network, the device will send its message to the default gateway address, which is the IP address of the router.
Local area network (LAN) and wide area network (WAN) definitions vary greatly, but in general, LANs are networks encompassing switches and hubs. Once a network traverses across a router, these networks are encompassed within a WAN.
Subnet specifics
As noted above, IP addresses in conjunction with subnet masks logically separate networks into subnets that typically do the same kind of work. Subnets are separated by routers, and messages can traverse across these routers through the default gateway address (router address). If two devices are on the same LAN and need to communicate with each other, their subnets must be compatible and their host addresses unique. If not, they cannot communicate with each other without the help of a router.
To determine whether two devices can communicate with each other on a LAN without a router, apply the subnet mask of each device to its respective IP address to see if the resulting network addresses are the same. If they are, they should be able to communicate. This calculation can be done manually, but there are many websites and mobile applications to assist.
For example, at www.subnet-calculator.com, one can simply enter the IP address and subnet mask, and it will calculate the range of possible devices that can communicate to each other. Another concept called network class is included with this tool. The network class is determined by whether there are many subnets with relatively few devices (hosts) or fewer networks with many hosts, such as the Internet. For most private networks inside of a company, Class B or Class C will be the network class of choice.
Remote access—routers and firewalls
Remote access speeds are increasing, reducing the need to be on-site for many monitoring, adjustment, and troubleshooting activities. However, accessing devices behind a router and firewall adds some complexities to how devices connect at a remote facility.
NAT stands for Network Address Translation. The purpose of NAT is to allow a facility to give many devices access to the Internet without requiring a public IP address for each one as there is a cost associated with each required public IP address. The router/firewall will translate the IP addresses of outgoing and incoming messages to and from the Internet so that anyone outside of the company network will only see the public IP address.
Port Forwarding is a feature of a router/firewall allowing messages coming from the Internet to go to a specific device on the inside of that network. Outgoing messages get handled automatically. The router keeps track of where a message originated from within the network by means of the port number and matches up the response to the original message. But a router does not know where to send an incoming message simply by means of the IP address as the device originating the message does not know the internal IP addresses of all the devices. The port number is used for this purpose.
The router has a configuration table that allows the user to determine the correct internal IP address by specifying the port number receiving the message. But Port Forwarding is not the most secure method of allowing remote access because opening up a port can open up a door for other devices to come in and cause trouble.
Securing Traffic- VPN
A VPN is a far more secure way to access devices remotely. A virtual private network (VPN) connects to a router/firewall with VPN server capability from a remote device that makes it look like they coexist on the same local network. A connection is established between the local and remote devices by means of a local VPN router, or through use of a VPN client software tool that runs on a PC or device. Once connected, the VPN server gives the remote device an IP address of the internal network, and the remote device can communicate to the devices on the internal network without routing.
Today VPN takes on many ways and forms. And with it some simple and others more complex. There are different ways to configure and connect a VPN, and these connections can be more complex and difficult to set up initially. But once this initial effort is completed, VPNs provide easier and more secure remote connectivity.
Today VPN provides one secure and hidden ID. This is one misuse method by hackers to hide who they are. There are several services that you can use. I try to block them when I can.
Wireshark hunts down problems
Wireshark is an old standby software for monitoring network traffic and is very useful on any local network for checking firewall compliance and hacker penetration. A neat tool and it’s free. Runs on Linux and Windows.
Switches have the ability to use port mirroring and one can specify a port to send all of the messages from one or more devices. Wireshark (https://wireshark.org) can be connected to this mirror port. Wireshark will grab and display all of the messages from those devices, which will show exactly what is occurring in the way of communications. Using the filter tools, one can narrow down the overwhelming traffic to a specific OSI layer, port, or IP. This tool is excellent and it is free…
#Networking Made Simple
Other stuff